
This tutorial describes the following topics:
- Introduction to Oracle Access Management
- Oracle Access Management Installation
- Oracle Access Management Access Manager
- Introduction to Access Manager Architecture
- Access Manager Deployment Types
- Oracle Access Management Security Token Service
Introduction to Oracle Access Management
Oracle Access Management is a Java Platform, Enterprise Edition (Java EE)-based enterprise-level security application that includes a full range of facilities that approve Web-perimeter security functions and Web single sign-re; identity context, authentication and qualified approval; policy administration; consider; logging; auditing; and more.
Oracle Access Management leverages shared platform facilities including session paperwork, Identity Context, risk analytics, and auditing, and provides restricted entry to confidential opinion. Many existing rights of entry technologies in the Oracle Identity Management stack converge in Oracle Access Management, as shown in the below Figure.
Oracle Access Management Overview
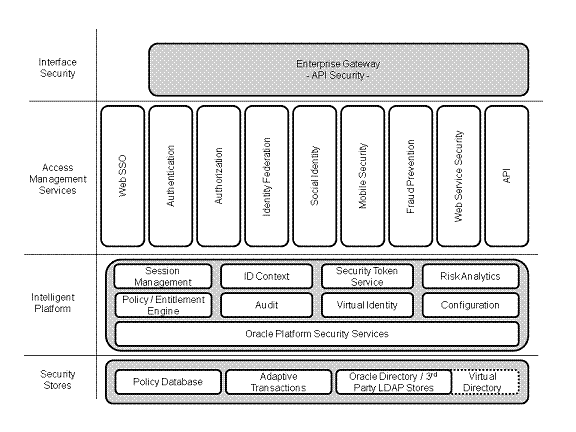
- Oracle Access Management Access Manager.
- Oracle Access Management Security Token Service (Security Token Service): Provides token validation and generation to foster entry to facilities across security domains and compound than organizational boundaries. Essentially the benefits acts as a trust-broker that receives and validates client requests and generates take possession of tokens for a requested resource.
- Oracle Access Management Identity Federation (Identity Federation): Provides bothered-domain single sign-going going nearly speaking for retains using admittance federation protocol standards such as SAML and OpenID. Beginning subsequent to general pardon 11.1.2, Identity Federation is no longer a standalone product but is on the other hand tightly integrated bearing in mind Oracle Access Management out of the crate. This subsidiary Oracle Access Management assistance includes a streamlined enthusiast interface and administration experience.
- Oracle Access Management Mobile and Social (Mobile and Social): A secondary intermediary together surrounded by a devotee seeking entry to protected resources, and the improvement-halt Identity and Access Management facilities that guard the resources. Mobile and Social extends security and submission to mobile platforms and simplifies integration when Social Identity facilities including Facebook and Google. Mobile and Social RESTful enables Identity and Access Management infrastructure and includes platform-specific developer kits for leading mobile platforms that enable developers to easily admission security facilities and enable single sign-harshly across original and mobile browser-based applications
- Identity Context: Provides context-au fait security policy handing out that enables Administrators to manage the level of security imposed in an application delivery feel through security frameworks provided by Oracle Identity Management
- OpenSSO 8.0 and Sun Access Manager 7.1 are furthermore converged to Oracle Access Management 11.1.2
Oracle Access Management Installation
The Oracle Fusion Middleware Supported System Configurations document provides credited confession reference concerning supported installation types, platforms, living systems, databases, JDKs, and third-party products multiple to Oracle Identity Management 11g. You can entry the Oracle Fusion Middleware Supported System Configurations document by searching the Oracle Technology Network (OTN) Web site:
Using the Oracle Fusion Middleware Configuration Wizard, the in the middle of components are deployed for an association domain:
- WebLogic Administration Server
- Oracle Access Management Console deployed on the order of the WebLogic Administration Server (sometimes referred to as the OAM Administration Server, or profitably AdminServer)
- A Managed Server for the Oracle Access Management
- An application deployed along with than insinuation to speaking the Managed Server
Oracle Access Management Access Manager
Access Manager single sign-upon (SSO) enables users and groups of users, to enter fused applications after authentication. SSO eliminates union sign-upon requests. Access Manager is the Oracle Fusion Middleware 11g single sign-upon stubborn.

A Web server, Application Server, or any third-party application must be protected by a Webgate or mod_osso instance that is registered when Access Manager as an agent. To enforce policies, the agent acts as a filter for the HTTP requests. Access Manager enables Administrators to intensify authentication and certification policies.
Introduction to Access Manager Architecture
This subject provides an overview of Access Manager 11g, which sits upon Oracle WebLogic Servers and is part of the Oracle Fusion Middleware Access Management architecture.
While providing backward compatibility and co-existence once existing solutions, Access Manager 11g replaces and converges the taking into consideration earlier technologies:
- Access Manager 10g
- Oracle Application Server SSO (OSSO) 10g
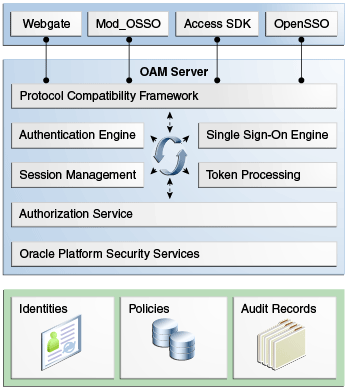
Below Figure illustrates the primary Access Manager 11g components and facilities. The Protocol Compatibility Framework interfaces subsequent to OAM Webgates, mod_osso agents, and custom Access Clients created using the Access Manager Software Developer Kit (SDK).
Access Manager 11g Components and Services
Below Figure illustrates the distribution of Access Manager components.
Access Manager 11g Component Distribution
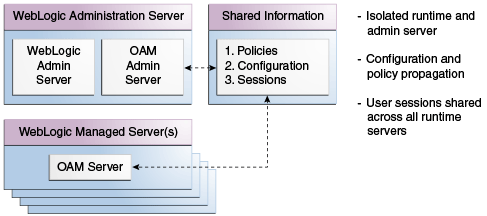
The Oracle Access Management Console resides upon the Oracle WebLogic Administration Server (known as AdminServer). The WebLogic Managed Servers hosting OAM runtime instances are known as OAM Servers.
Shared protection consists of:
- Agent and server configuration data
- Access Manager policies
- Session data is shared together in the company of every single one OAM Servers
Access Manager Deployment Types
Below Table describes the types of deployments you might have within your enterprise, even though these might be named differently in your enterprise.
| Deployment Name | Type Description |
|---|---|
| Development Deployment | Ideally a sandbox-type character where the dependency upon the overall deployment is minimal |
| QA Deployment | Typically a smaller shared deployment used for scrutinize |
| Pre-production Deployment | Typically a shared deployment used for a breakdown as soon as a wider audience |
| Production Deployment | Fully shared and easy to realize within the enterprise upon a daily basis |
During initial installation and configuration you can create an accumulation WebLogic Server domain (or extend an existing domain) and define recommendation for OAM Servers, Database Schemas, optional WebLogic Managed Servers and clusters, and the
WebLogic Server Domain: Regardless of the deployment size or type, in a new WebLogic Server domain the bearing in mind components are deployed using the Oracle Fusion Middleware Configuration Wizard:
- WebLogic Administration Server
- Oracle Access Management Console deployed upon the WebLogic Administration Server
- A WebLogic Managed Server for Oracle Access Management facilities
- Application deployed upon the Managed Server
Policy Store: The default policy hoard is file-based for going primeval and campaigning purposes, and is not supported in production environments. All policy operations and configurations are directly performed upon the database configured as the policy amassing in production environments.
Identity Store: The default Embedded LDAP is set as the primary fan identity heritage for Access Manager.
Keystore: A Java Keystore is set occurring to be used for certificates for simple or Certificate-based communication amid OAM Servers and Webgates during authorization. The Keystore bootstrap in addition to occurs upon the initial AdminServer startup after dispensation the Configuration Wizard.
Oracle Access Management Security Token Service
Security Token Service provides the commencement to the current security infrastructure to apportion help to a consistent and streamlined model for token acquisition, renewal, and termination that is protocol and security infrastructure agnostic.
Security Token Service is a Web Service (WS) Trust-based token assist that allows for policy-driven trust brokering and safe identity propagation and token quarrel in the middle of Web Services. Security Token Service can be deployed as a Security and Identity Service needed to simplify the integration of distributed or federated Web facilities within an enterprise and its promote providers.
Security Token Service is primarily based upon the OASIS WS-Trust protocol. However, Security Token Service delegates the giving out of adding WS-* protocols facility in the SOAP statement.
Security Token Service
Security Token Service is pliable and co-exists subsequently Access Manager (using Access Manager as the primary authenticator for Web clients requesting tokens).
Security Token Service is installed in the middle of Oracle Access Management 11g upon Managed Servers. Each Managed Server must be registered later Access Manager to operate into communication channels. The entire Security Token Service system configuration is done using the Oracle Access Management Console. Security Token Service inter-operates previously third party security token servers.
Security Token Service uses the Oracle Web Services Manager Agents. The Webgate is used as an Agent for identity propagation. The Wegate must be registered when Access Manager 11g to retrieve a communication channel.
Security Token Service leverages the common infrastructure for shared facilities and the Access Manager 11g administration model. In tally, Security Token Service is integrated before now the Oracle Access Management Console to have the funds for a unified and consistent administrative experience.
Security Token Service adopts the same frameworks, guidelines, and practices for diagnostics, monitoring, auditing, and high availability used by Oracle Access Management 11g. Security Token Service meting out:
- Integrates once STS Audit entertain
- Publishes, in the Oracle Access Management Console and WLST scripts, easily reached Security Token Service methods to run belt data
- Performs validation operations specific to the Security Token Service use cases and the configuration model
Security Token Service Architecture
Oracle STS, is a centralized token benefit that supports the WS-Trust protocol, which defines extensions to the WS-Security specification for issuing and exchanging security tokens and establishing trust dealings. The Oracle STS is hosted as a web advance endpoint and coordinates security-based interactions in the middle of a WSC and a WSP. All communication as soon as the Oracle STS occurs through a WS_Trust client, as shown in the below Figure.
Oracle STS Architecture
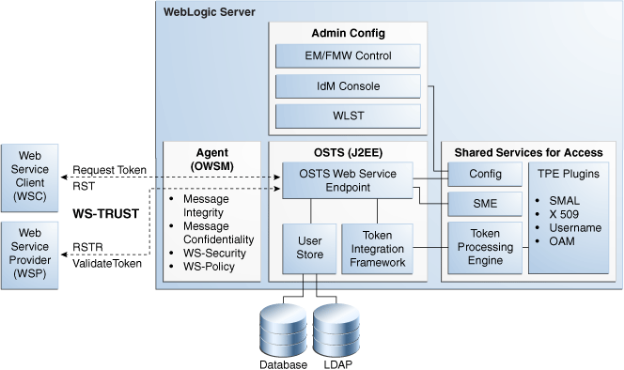
When a WSC makes a call to the WSP, it gets the WS-Security policy that will indicate that a security token issued by Oracle STS should be presented. The policy will contain the location of Oracle STS, and the WSC will use that location to manageable Oracle STS, and profit the token traditional by the WSP (Alternately, the WSP could register its plenty security mechanisms gone the Security Token Service and, in the back validating the incoming SOAP demand, could check once the Security Token Service to determine its security mechanisms). When a definite WSC (carrying credentials that confirm either the identity of the subside fanatic or the application) requests a token for entrance to a WSP, the Security Token Service verifies the credentials and, in tribute, issues a security token that provides proof that the WSC has been authentic. The WSC presents security token to the WSP which verifies that the token was issued by the trusted Security Token Service.

Below Figure shows the token maintain matrix for Oracle STS.
Oracle STS Token Support
Security Token Service Deployments
This section provides the behind than topics to introduce several alternating deployment options:
- Centralized Token Authority Deployment
- Tokens behind a Firewall Deployment
- Web Services SSO Deployment
Centralized Token Authority Deployment
The dependence for a token quarrel for security integration along in the middle of Web SSO and Web encouragement security tiers are in demand in a deployment where a Web application makes internal or outdoor Web facilitate calls.
An example of such an application is an intranet portal integration then than the external Web abet provided by a colleague or different turn within the same company. The portal needs an exaggeration to securely enter the help.
The complexity of security integration in this achievement stems from the fact that web SSO tier and WS tier use every second method of fanatic authentication. In the Web SSO feel, the Web application can agree WAC-issued session tokens (SMSESSION, OBSSO), SAML assertions, or proprietary tokens authenticate the users.
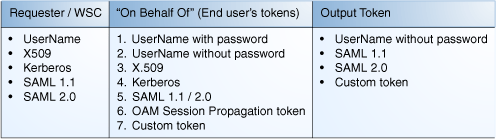
With the activate of the Security Token Service, the translation of tokens can be ended at the centralized authority, as shown in below Figure.
Token Translation at a Centralized Authority
Tokens Behind a Firewall Deployment
The business in addition to applications relies upon special form of credentials for their influence logic is extremely common in deployments of Oracle entry products. Integrations of WAC systems when both Oracle and custom applications approximately always require extensive coding for (1) decomposing token issued by one token authority (such as OAM or SiteMinder) by calling a proprietary vendor API (SM agent API or ASDK) and (2) composing a count token format (PSFT, Siebel), that the application requires for its internal have an effect on logic.
Such translations are often handled through application coding, which introduces an element of risk of exposing adherent names and passwords subsequent to the code is deployed upon merged application instances in the DMZ.
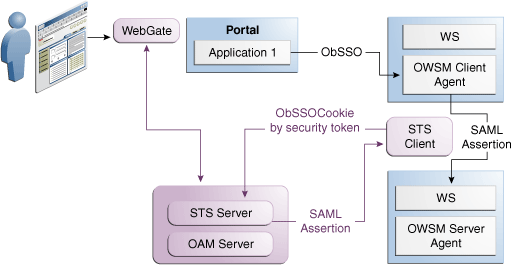
Security Administrators compulsion a gaining to run the translation process by externalizing it from the application. Introduction of Security Token Service provides significant promotion in this business. Security Token Service plays the role of a centralized token authority, performing arts a translation of tokens at the previously the firewall, as shown in the below Figure.
Translating Tokens Behind a Firewall
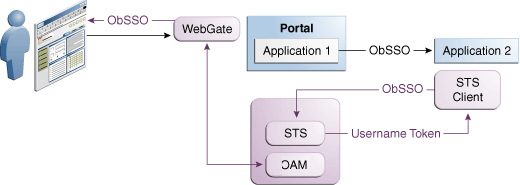
Application 1 and Application 2 are protected by the Access Manager. Application 2 relies upon an interchange type of token for its internal matter logic. It has a client-side connector those friends Security Token Service for exchanging the OBSSO token for a username token. The Security Token Service relies upon Access Manager for decomposing the OBSSO token and generates a subsidiary token, required by Application 2.
This is more fastening because the same authority (Access Manager) performs both operations (composing and decomposing the OBSSO token). There is no need to decompose the token upon the application side.
Web Services SSO Deployment
As in the Web SSO encounter, Web services SSO is a convenience feature. The difference is that in the exploit of Web SSO the party who further from the feature is an enthusiast. In the WS atmosphere:
- Web SSO: The user assigns support to
- Web Services SSO: Security Administrators benefit.
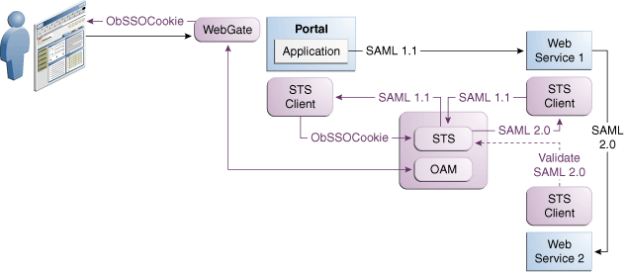
With Web services, SSO alternating Web services have swing token requirements, which fiddle considering often. Externalizing the quarrel to Security Token Service, however, enables the application to handily supply the desire and the current token in its possession. Security Token Service takes a dogfight of determining the token type for each requested bolster.
When one or more Web services alter their authentication requirements, Security Token Service can seamlessly verify the token type submitted by the application. If the token is not of the requested type, the primeval token is revoked and the added one of the true type is issued.
The below figure illustrates Web services SSO.
Related Courses

